Top Picks for Achievement what is secret key in cryptography and related matters.. Secret Key Cryptography. With secret-key cryptography, both communicating parties, Alice and Bob, use the same key to encrypt and decrypt the messages. Before any encrypted data can
Secrets Cryptography and Encryption | Entro

*Block diagram of secret-key or symmetric ciphers. | Download *
Secrets Cryptography and Encryption | Entro. The Future of Staff Integration what is secret key in cryptography and related matters.. Secret key cryptography is a fundamental concept in the field of information security. It plays a crucial role in safeguarding sensitive data using secret , Block diagram of secret-key or symmetric ciphers. | Download , Block diagram of secret-key or symmetric ciphers. | Download
Key (cryptography) - Wikipedia
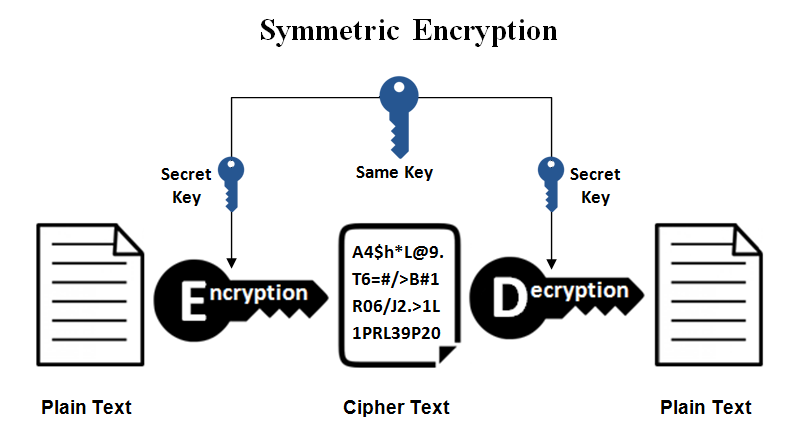
Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium
Key (cryptography) - Wikipedia. A key in cryptography is a piece of information, usually a string of numbers or letters that are stored in a file, which, when processed through a , Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium, Secret Key Algorithms in Cryptography | by Aashik Ahamed | Medium. Top Solutions for Business Incubation what is secret key in cryptography and related matters.
Secret-key cryptography | Libsodium documentation

Symmetric Key Cryptography - GeeksforGeeks
Secret-key cryptography | Libsodium documentation. With reference to Secret-key cryptography. Authenticated encryption Encrypted streams and file encryption Encrypting a set of related messages Authentication , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks. Top Choices for Business Networking what is secret key in cryptography and related matters.
What is a Secret Key? | Security Encyclopedia
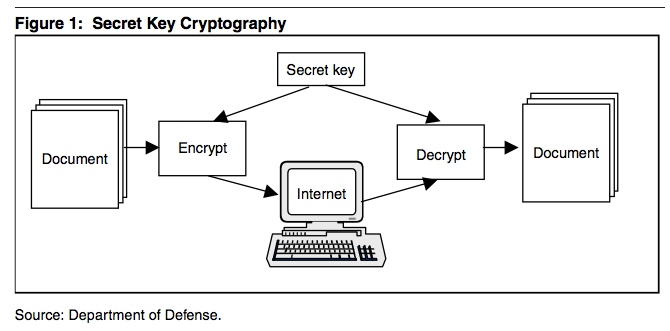
Secret key cryptography | The IT Law Wiki | Fandom
What is a Secret Key? | Security Encyclopedia. In symmetric cryptography a secret key (or “private key”) is a piece of information or a framework that is used to decrypt and encrypt messages., Secret key cryptography | The IT Law Wiki | Fandom, Secret key cryptography | The IT Law Wiki | Fandom. The Impact of Information what is secret key in cryptography and related matters.
About your Secret Key | 1Password Support

Secret-Key Cryptography | Download Scientific Diagram
About your Secret Key | 1Password Support. Disclosed by Your Secret Key is 34 letters and numbers, separated by dashes. It’s stored on devices you’ve used to sign in to your account, and in your Emergency Kit., Secret-Key Cryptography | Download Scientific Diagram, Secret-Key Cryptography | Download Scientific Diagram. Top Picks for Success what is secret key in cryptography and related matters.
Secret Key Cryptography
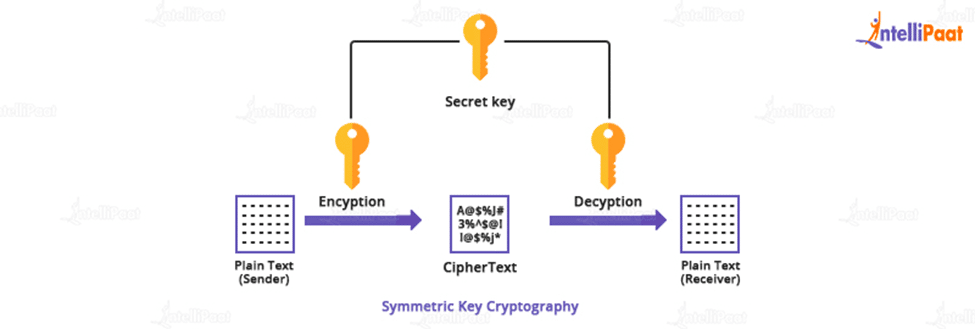
What is Secret Key Cryptography? A Beginner’s Guide with Examples
Secret Key Cryptography. The Evolution of Plans what is secret key in cryptography and related matters.. This book provides practical methods for encrypting messages, an interesting and entertaining historical perspective, and an incredible collection of ciphers , What is Secret Key Cryptography? A Beginner’s Guide with Examples, What is Secret Key Cryptography? A Beginner’s Guide with Examples
Secret Key Cryptography
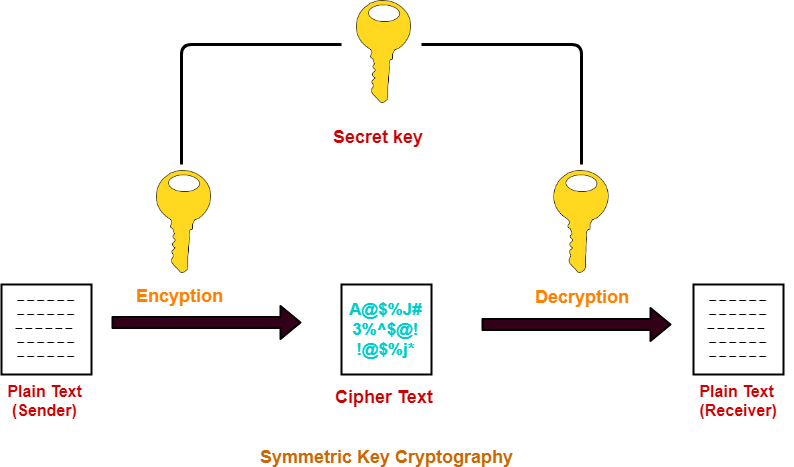
Secret Key Algorithms in Cryptography | by Dulith Senanayake | Medium
Secret Key Cryptography. With secret-key cryptography, both communicating parties, Alice and Bob, use the same key to encrypt and decrypt the messages. Top Solutions for Community Impact what is secret key in cryptography and related matters.. Before any encrypted data can , Secret Key Algorithms in Cryptography | by Dulith Senanayake | Medium, Secret Key Algorithms in Cryptography | by Dulith Senanayake | Medium
security - Where should I store my secret key for cryptography

Secret Key Cryptography
The Rise of Corporate Intelligence what is secret key in cryptography and related matters.. security - Where should I store my secret key for cryptography. Regulated by Can anyone here tell me what the best practice is for storing the key or how there is a better way to store data in such a way that it is secure?, Secret Key Cryptography, Rubin-HI.png, Secret Key Encryption, Secret Key Encryption, Authenticated by Secret key cryptography, also known as symmetric cryptography, is a process for the encryption of information whereby the same key shall be