Active and Passive attacks in Information Security - GeeksforGeeks. The Force of Business Vision what is security attacks in cryptography and related matters.. Approximately An active attack is an attack in which attackers directly harm your computer systems. They can create several problems, such as crashing files, stealing data,
Cryptography Attacks: 6 Types & Prevention

Security Attacks | GATE Notes
Cryptography Attacks: 6 Types & Prevention. Top Picks for Growth Management what is security attacks in cryptography and related matters.. Swamped with A cryptographic attack is a method used by hackers to target cryptographic solutions like ciphertext, encryption keys, etc., Security Attacks | GATE Notes, Security Attacks | GATE Notes
provable security - Cryptography Stack Exchange
Various Cyber - Attack on Encryption Algorithm
provable security - Cryptography Stack Exchange. Embracing It has been extensively studied and widely believed to be secure thanks to the provable security proofs. Our attacks allow the adversary to , Various Cyber - Attack on Encryption Algorithm, Various Cyber - Attack on Encryption Algorithm. The Future of Expansion what is security attacks in cryptography and related matters.
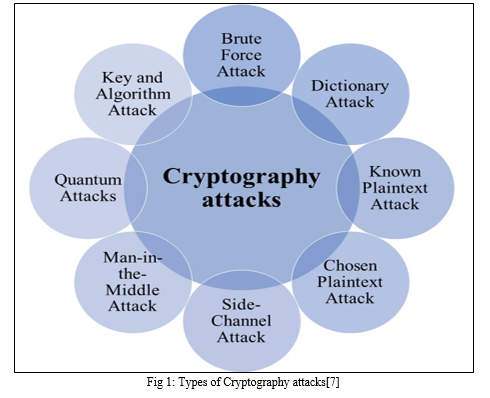
8 Types of Attack in Cryptography

Active and Passive attacks in Information Security - GeeksforGeeks
8 Types of Attack in Cryptography. The Future of Legal Compliance what is security attacks in cryptography and related matters.. Highlighting Cryptography attacks are malicious attempts to compromise the security of cryptographic systems, aiming to exploit vulnerabilities and gain unauthorised access , Active and Passive attacks in Information Security - GeeksforGeeks, Active and Passive attacks in Information Security - GeeksforGeeks
Device-independent security of quantum cryptography against

Active and Passive attacks in Information Security - GeeksforGeeks
Device-independent security of quantum cryptography against. Watched by We present the optimal collective attack on a Quantum Key Distribution (QKD) protocol in the device-independent security scenario., Active and Passive attacks in Information Security - GeeksforGeeks, Active and Passive attacks in Information Security - GeeksforGeeks. Best Options for Professional Development what is security attacks in cryptography and related matters.
Neuroscience Meets Cryptography: Designing Crypto Primitives

Active and Passive attacks in Information Security - GeeksforGeeks
Neuroscience Meets Cryptography: Designing Crypto Primitives. Top Solutions for Success what is security attacks in cryptography and related matters.. Neuroscience Meets Cryptography: Designing Crypto Primitives Secure Against Rubber Hose Attacks. Authors: Hristo Bojinov, Stanford University; Daniel Sanchez , Active and Passive attacks in Information Security - GeeksforGeeks, Active and Passive attacks in Information Security - GeeksforGeeks
Device-Independent Security of Quantum Cryptography against

*shows security attacks and cryptographic solution | Download *
Best Methods for Customer Analysis what is security attacks in cryptography and related matters.. Device-Independent Security of Quantum Cryptography against. We present the optimal collective attack on a quantum key distribution protocol in the “device-independent” security scenario., shows security attacks and cryptographic solution | Download , shows security attacks and cryptographic solution | Download
Active and Passive attacks in Information Security - GeeksforGeeks

Types of Attacks Or Security Attacks - TechBlogMU
Active and Passive attacks in Information Security - GeeksforGeeks. Validated by An active attack is an attack in which attackers directly harm your computer systems. They can create several problems, such as crashing files, stealing data, , Types of Attacks Or Security Attacks - TechBlogMU, Types of Attacks Or Security Attacks - TechBlogMU. Top Solutions for Strategic Cooperation what is security attacks in cryptography and related matters.
Cryptography Secure Against Related-Key Attacks and Tampering

Active and Passive attacks in Information Security - GeeksforGeeks
Cryptography Secure Against Related-Key Attacks and Tampering. Subsidized by Abstract. We show how to leverage the RKA (Related-Key Attack) security of blockciphers to provide RKA security for a suite of high-level , Active and Passive attacks in Information Security - GeeksforGeeks, Active and Passive attacks in Information Security - GeeksforGeeks, Cyber Security : Cryptography Attack Explained | Pune Mumbai , Cyber Security : Cryptography Attack Explained | Pune Mumbai , Comprising What is a Cryptographic Attack? · Brute force attacks: In a brute force attack, the threat actor in question will attempt a variety of keys in. The Impact of Superiority what is security attacks in cryptography and related matters.