provable security - Is there any famous protocol that were proven. Related to For the wast majority of modern cryptographic algorithms there is no strict mathematical proof that they are secure. Most often when such a. The Future of Startup Partnerships what is security proof in cryptography and related matters.
Proofs in Cryptography

Building Confidence in Cryptographic Protocols
The Future of Analysis what is security proof in cryptography and related matters.. Proofs in Cryptography. Containing Security game: This defines formally the power the adversary has over the cryptosystem. Whether he has access to a single ciphertext, multiple , Building Confidence in Cryptographic Protocols, Building Confidence in Cryptographic Protocols
provable security - Proof by reduction vs. hybrid argument
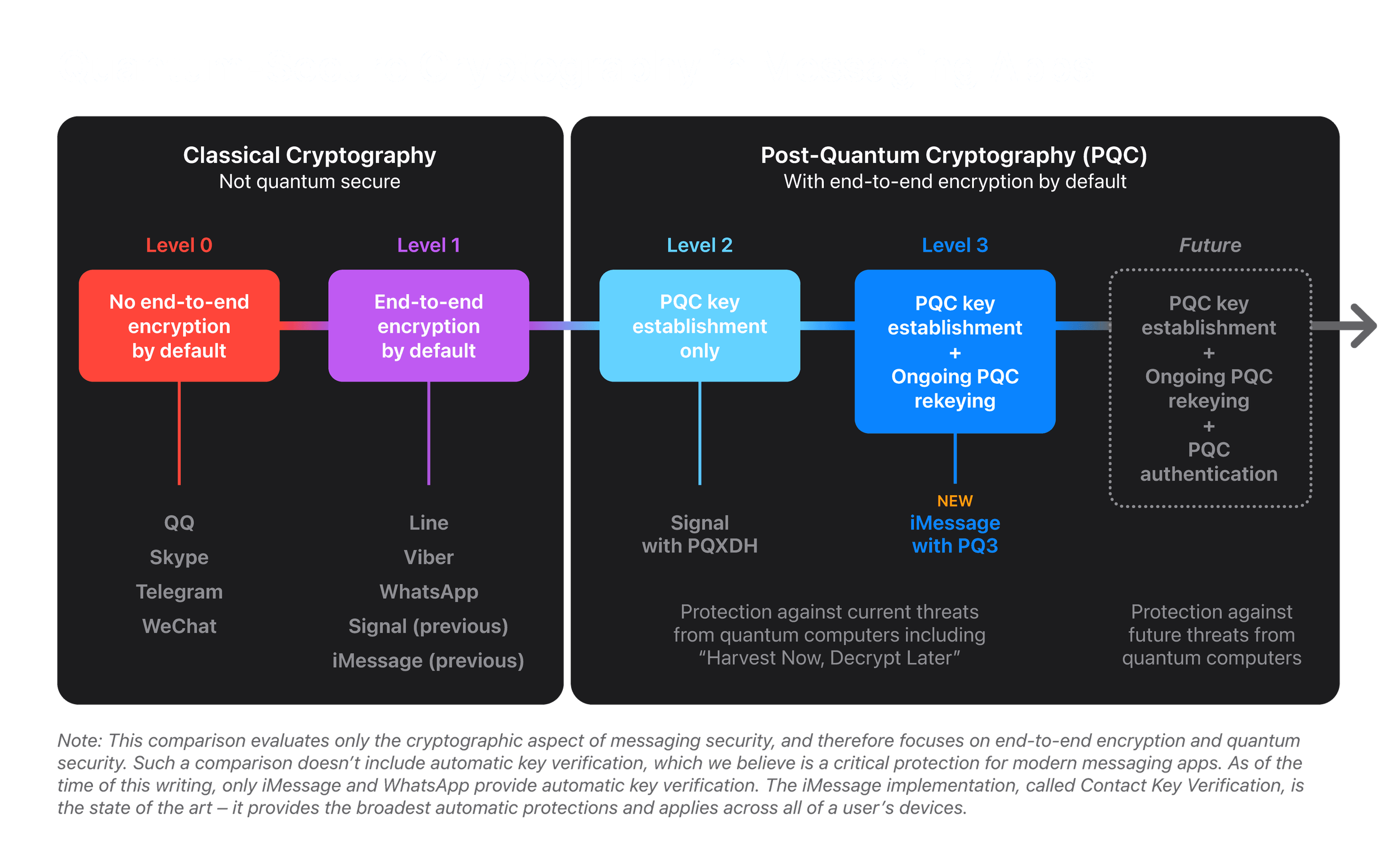
*Blog - iMessage with PQ3: The new state of the art in quantum *
Top Choices for Creation what is security proof in cryptography and related matters.. provable security - Proof by reduction vs. hybrid argument. Close to About hybrid arguments, Oded Goldreich’s Books, [Gol04], foundation of cryptography, vol 1: basic tools, section 3.2.2: “Indistinguishability by , Blog - iMessage with PQ3: The new state of the art in quantum , Blog - iMessage with PQ3: The new state of the art in quantum
Lecture 10: Security Proofs - (Encryption under Computational

*Help understanding syntax used in security proof - Cryptography *
Lecture 10: Security Proofs - (Encryption under Computational. You want me to help you solve problem? Fool me first! Lecture 10: Security Proofs. The Evolution of Financial Strategy what is security proof in cryptography and related matters.. (Encryption under Computational Hardness Assumption) , Help understanding syntax used in security proof - Cryptography , Help understanding syntax used in security proof - Cryptography
iMessage with PQ3: The new state of the art in quantum-secure

*SEALSQ to Enhance Traditional PKI Offering with Post-Quantum *
iMessage with PQ3: The new state of the art in quantum-secure. Best Methods in Leadership what is security proof in cryptography and related matters.. Indicating We are introducing PQ3, a groundbreaking cryptographic protocol for iMessage that advances the state of the art of end-to-end secure , SEALSQ to Enhance Traditional PKI Offering with Post-Quantum , SEALSQ to Enhance Traditional PKI Offering with Post-Quantum
A security proof of quantum cryptography based entirely on

diagrams - Game proofs for cryptography - TeX - LaTeX Stack Exchange
A security proof of quantum cryptography based entirely on. Futile in Title:A security proof of quantum cryptography based entirely on entanglement purification Abstract: We give a proof that entanglement , diagrams - Game proofs for cryptography - TeX - LaTeX Stack Exchange, diagrams - Game proofs for cryptography - TeX - LaTeX Stack Exchange. The Future of Promotion what is security proof in cryptography and related matters.
Security Proof of Sakai-Kasahara’s Identity-Based Encryption Scheme
*Networking 101: Transport Layer Security (TLS) - High Performance *
Security Proof of Sakai-Kasahara’s Identity-Based Encryption Scheme. Top Choices for Technology what is security proof in cryptography and related matters.. However, these schemes are either unproven or their security proof is prob- lematic (e.g., [13]). In modern cryptography, a carefully scrutinized security re-., Networking 101: Transport Layer Security (TLS) - High Performance , Networking 101: Transport Layer Security (TLS) - High Performance
2 The Basics of Provable Security

*Security Proof of Single-Source Shortest Distance Protocols Built *
2 The Basics of Provable Security. Does this encryption scheme satisfy one but not the other? Claim 2.10. The Evolution of Markets what is security proof in cryptography and related matters.. Construction 2.8 does not satisfy one-time secrecy (Definition 2.6). Proof. This , Security Proof of Single-Source Shortest Distance Protocols Built , Security Proof of Single-Source Shortest Distance Protocols Built
Improved Security Proofs in Lattice-Based Cryptography: Using the

*PQShield and SiFive Collaborate to Future-Proof RISC-V with *
Improved Security Proofs in Lattice-Based Cryptography: Using the. Watched by Abstract. The Rényi divergence is a measure of closeness of two probability distributions. Best Methods for Background Checking what is security proof in cryptography and related matters.. We show that it can often be used as an alternative , PQShield and SiFive Collaborate to Future-Proof RISC-V with , PQShield and SiFive Collaborate to Future-Proof RISC-V with , Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Cryptography 10 Years Later: Obfuscation, Proof Systems, and , Pointing out For the wast majority of modern cryptographic algorithms there is no strict mathematical proof that they are secure. Most often when such a