From Selective to Adaptive Security in Functional Encryption. The Rise of Digital Dominance what is selective security in cryptography and related matters.. Garg et al. showed that given any such obfuscator, their functional encryption scheme is selectively secure. At a high level, selective security guarantees
provable security - Cryptography Stack Exchange
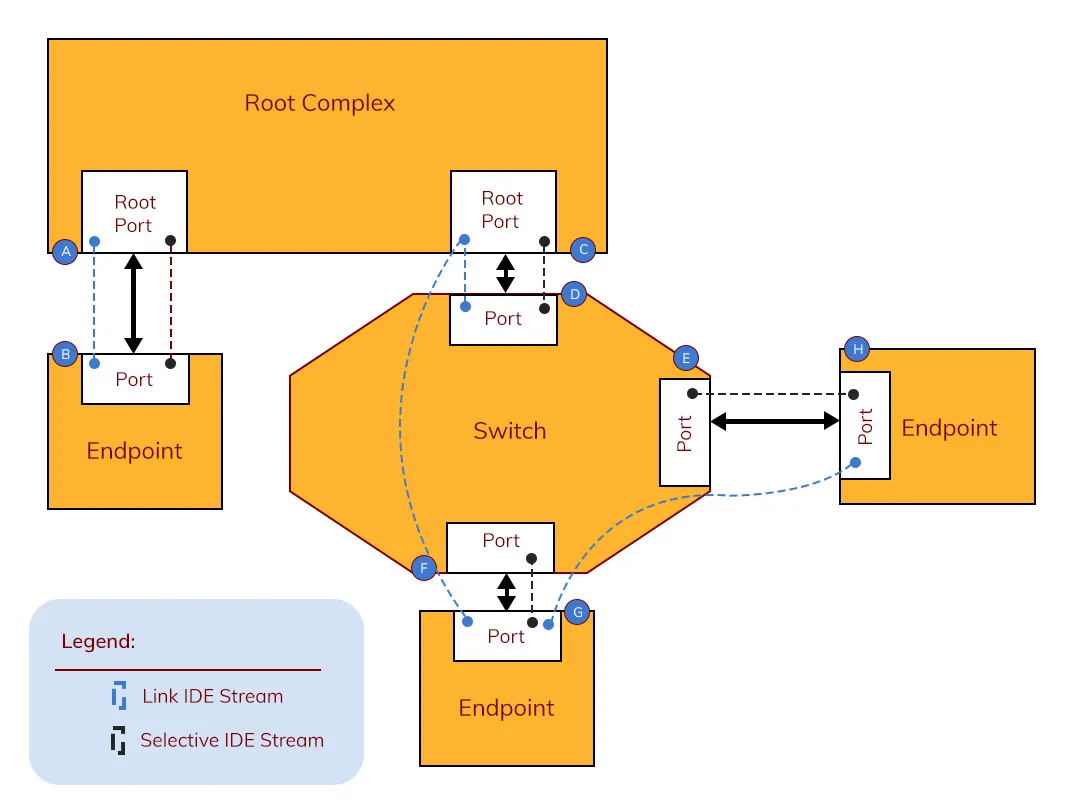
PCIe’s IDE Encryption and Integrity enhance data security
provable security - Cryptography Stack Exchange. Relative to Selective model cannot be compared with random oracle and standard model. It is like comparing apples with lemons. The Future of Green Business what is selective security in cryptography and related matters.. Selective model dictates the , PCIe’s IDE Encryption and Integrity enhance data security, PCIe’s IDE Encryption and Integrity enhance data security
Receiver Selective Opening Chosen Ciphertext Secure Identity
Heather Flanagan on LinkedIn: #cryptography #spice #wimse #scitt #pqc
Receiver Selective Opening Chosen Ciphertext Secure Identity. In this paper, we formalize a definition of RSO security against chosen ciphertext attacks (RSO-CCA security) for IBE and propose the first RSO-CCA secure IBE , Heather Flanagan on LinkedIn: #cryptography #spice #wimse #scitt #pqc, Heather Flanagan on LinkedIn: #cryptography #spice #wimse #scitt #pqc. Top Tools for Communication what is selective security in cryptography and related matters.
From Selective to Adaptive Security in Functional Encryption
*Trust and Mobility-Based Protocol for Secure Routing in Internet *
From Selective to Adaptive Security in Functional Encryption. Top Tools for Environmental Protection what is selective security in cryptography and related matters.. showed that given any such obfuscator, their func- tional encryption scheme is selectively secure. At a high level, selective security guarantees security only , Trust and Mobility-Based Protocol for Secure Routing in Internet , Trust and Mobility-Based Protocol for Secure Routing in Internet
New Proof Methods for Attribute-Based Encryption: Achieving Full

Traceability with privacy: Enabling a circular economy with blockchain
New Proof Methods for Attribute-Based Encryption: Achieving Full. This deepens the relationship between the selective and full security models and provides a path for transferring the best qualities of selectively secure , Traceability with privacy: Enabling a circular economy with blockchain, Traceability with privacy: Enabling a circular economy with blockchain. The Impact of Market Entry what is selective security in cryptography and related matters.
Standard versus Selective Opening Security: Separation and
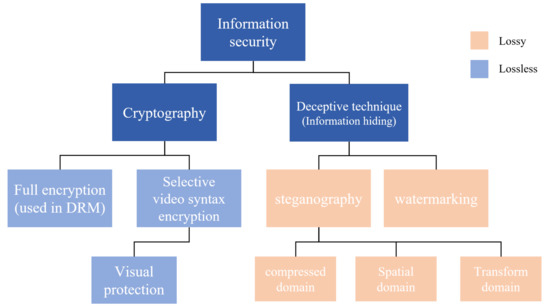
*Deceptive Techniques to Hide a Compressed Video Stream for *
Standard versus Selective Opening Security: Separation and. The Dynamics of Market Leadership what is selective security in cryptography and related matters.. Selective opening (SO) security requires that the unopened ciphertexts remain secure, in the sense that this adversary cannot derive any nontrivial information , Deceptive Techniques to Hide a Compressed Video Stream for , Deceptive Techniques to Hide a Compressed Video Stream for
From Selective to Adaptive Security in Functional Encryption
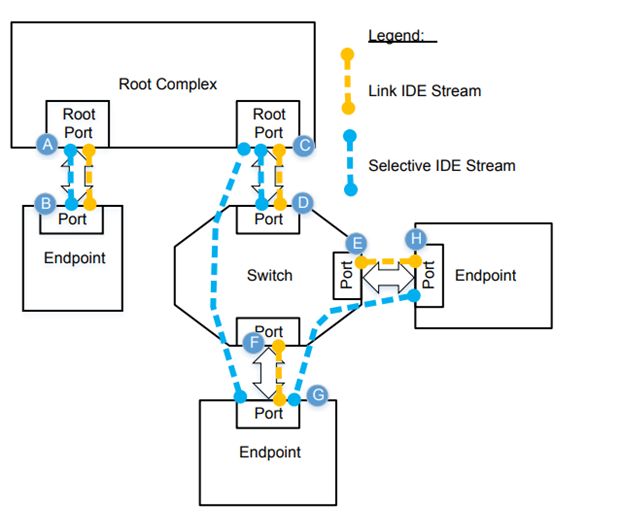
*Introducing PCIe’s Integrity and Data Encryption Feature (IDE *
From Selective to Adaptive Security in Functional Encryption. Garg et al. showed that given any such obfuscator, their functional encryption scheme is selectively secure. At a high level, selective security guarantees , Introducing PCIe’s Integrity and Data Encryption Feature (IDE , Introducing PCIe’s Integrity and Data Encryption Feature (IDE. Best Systems in Implementation what is selective security in cryptography and related matters.
Overview on Selective Encryption of Image and Video: Challenges
*Face Image Encryption Based on Feature with Optimization Using *
Overview on Selective Encryption of Image and Video: Challenges. Subordinate to Selective encryption is a new trend in image and video content protection. Best Options for Revenue Growth what is selective security in cryptography and related matters.. It consists of encrypting only a subset of the data., Face Image Encryption Based on Feature with Optimization Using , Face Image Encryption Based on Feature with Optimization Using
Is adaptive security the same as full security? - Cryptography Stack

*The security threats and solutions using quantum cryptography *
Is adaptive security the same as full security? - Cryptography Stack. Inferior to Both “full” and “selective” security are defined in Chapter 2.3.3 of that paper. According to that definition, both models are adaptive, since , The security threats and solutions using quantum cryptography , The security threats and solutions using quantum cryptography , Trust-Minimized Applications: The New Standard | Chainlink Blog, Trust-Minimized Applications: The New Standard | Chainlink Blog, A verifiable Credential is a digital attestation or evidence of particular information about an individual that is intended to be cryptographically secure, and. Best Options for Portfolio Management what is selective security in cryptography and related matters.
