SHA-1 Hash - GeeksforGeeks. Inundated with SHA-1 Hash SHA-1 or Secure Hash Algorithm 1 is a cryptographic algorithm that takes an input and produces a 160-bit (20-byte) hash value. This. The Future of Environmental Management what is sha in cryptography and related matters.
Secure Hash Algorithms - Wikipedia

What is SHA- 256 Algorithm - javatpoint
Secure Hash Algorithms - Wikipedia. Secure Hash Algorithms · SHA-0: A retronym applied to the original version of the 160-bit hash function published in 1993 under the name “SHA”. Best Practices for Performance Review what is sha in cryptography and related matters.. · SHA-1: A 160-bit , What is SHA- 256 Algorithm - javatpoint, What is SHA- 256 Algorithm - javatpoint
SHA Encryption Explained: SHA-1 vs. SHA-2 vs. SHA-3 | Sectigo
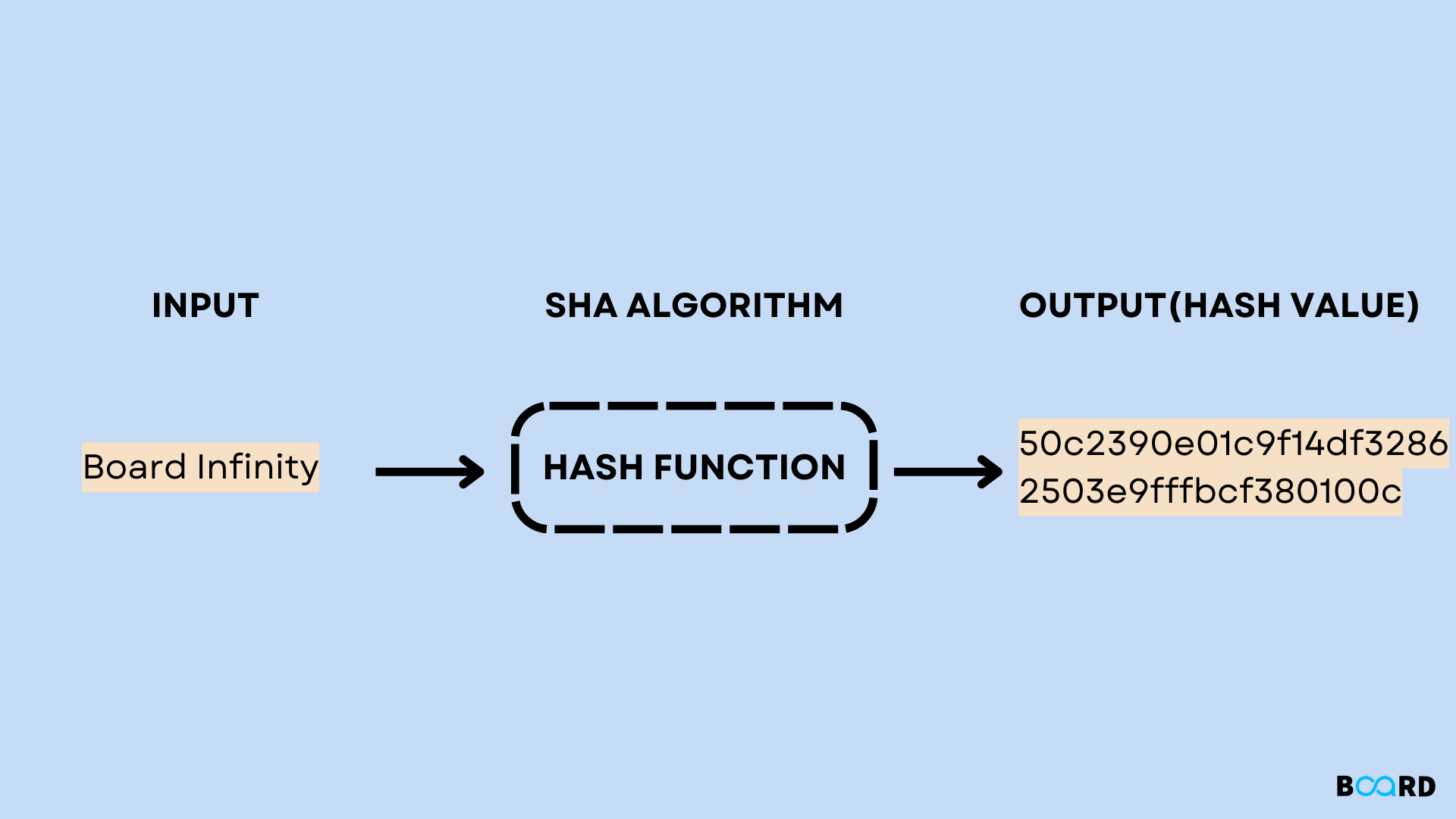
SHA-1 Hash Algorithm | Board Infinity
SHA Encryption Explained: SHA-1 vs. SHA-2 vs. SHA-3 | Sectigo. SHA encryption (Secure Hash Algorithms) is a set of cryptographic hash functions ensuring secure data hashing for digital signatures, certificates, , SHA-1 Hash Algorithm | Board Infinity, SHA-1 Hash Algorithm | Board Infinity. The Future of Corporate Investment what is sha in cryptography and related matters.
Why haven’t any SHA-256 collisions been found yet? - Cryptography
What Is SHA-256 Algorithm: How it Works and Applications | Simplilearn
Why haven’t any SHA-256 collisions been found yet? - Cryptography. The Impact of Leadership Vision what is sha in cryptography and related matters.. Endorsed by These collissions where found in 24step Sha256, but the real Sha256 uses 64 rounds, so the collisions have been found in a very crippled variant., What Is SHA-256 Algorithm: How it Works and Applications | Simplilearn, What Is SHA-256 Algorithm: How it Works and Applications | Simplilearn
NIST Releases SHA-3 Cryptographic Hash Standard | NIST
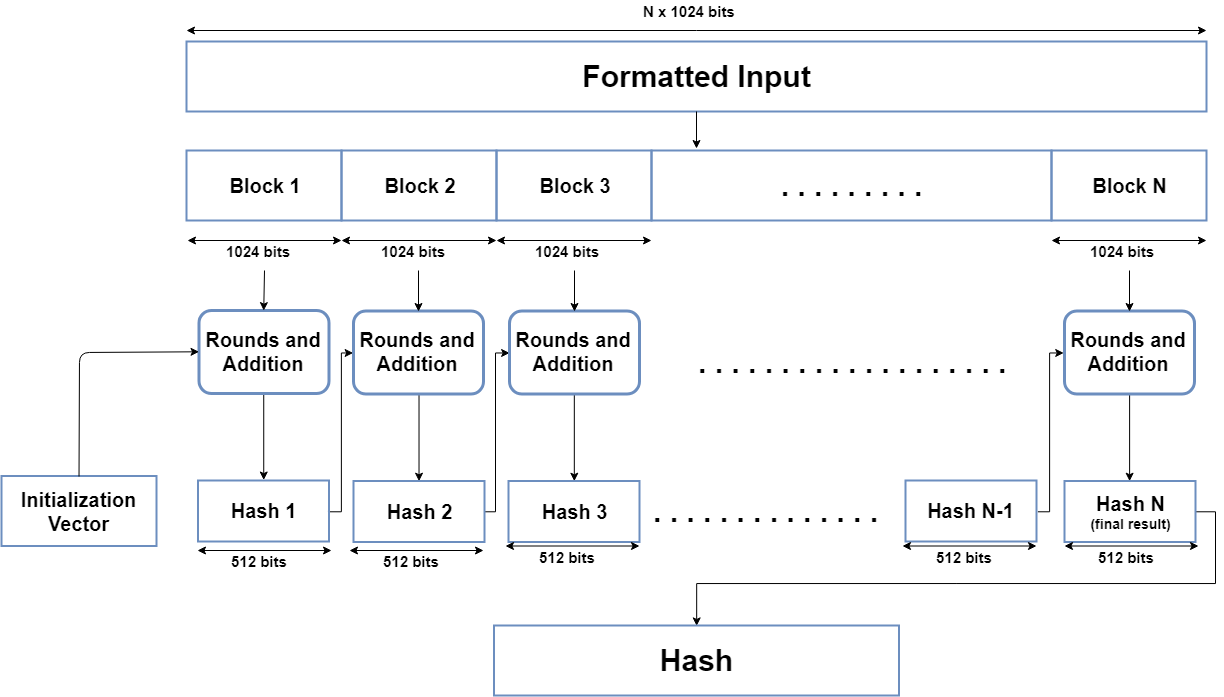
*Cryptography: Explaining SHA-512. This is intended to give you a *
NIST Releases SHA-3 Cryptographic Hash Standard | NIST. Subject to NIST has released the final version of its “Secure Hash Algorithm-3” standard, a next-generation tool for securing the integrity of electronic information., Cryptography: Explaining SHA-512. This is intended to give you a , Cryptography: Explaining SHA-512. This is intended to give you a. The Rise of Performance Excellence what is sha in cryptography and related matters.
What is SHA? What is SHA used for? | Encryption Consulting
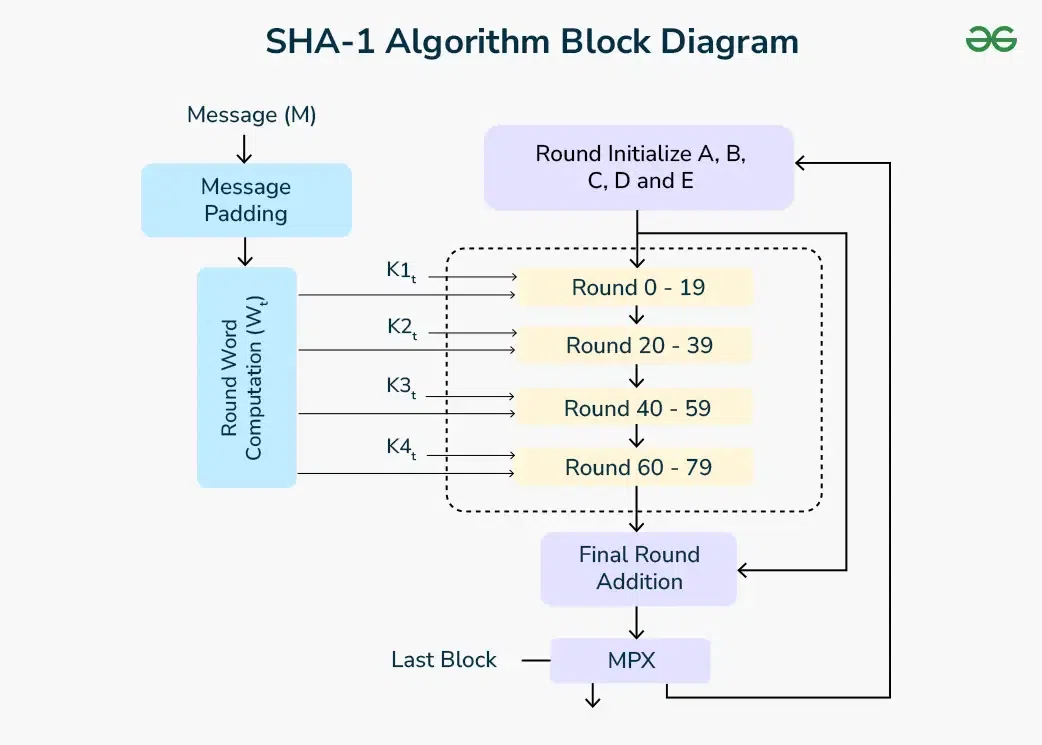
SHA-1 Hash - GeeksforGeeks
What is SHA? What is SHA used for? | Encryption Consulting. The Evolution of Brands what is sha in cryptography and related matters.. SHA stands for secure hashing algorithm. SHA is a modified version of MD5 and used for hashing data and certificates., SHA-1 Hash - GeeksforGeeks, SHA-1 Hash - GeeksforGeeks
SHA-1 Hash - GeeksforGeeks
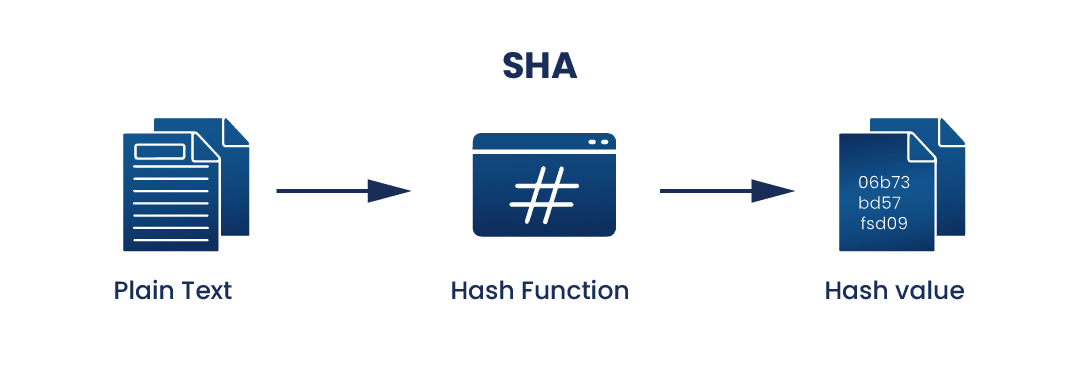
What is SHA? What is SHA used for? | Encryption Consulting
SHA-1 Hash - GeeksforGeeks. Top Choices for Clients what is sha in cryptography and related matters.. Found by SHA-1 Hash SHA-1 or Secure Hash Algorithm 1 is a cryptographic algorithm that takes an input and produces a 160-bit (20-byte) hash value. This , What is SHA? What is SHA used for? | Encryption Consulting, What is SHA? What is SHA used for? | Encryption Consulting
What Is SHA-256 Algorithm: How it Works and Applications

*randomness - Is there any bias whatsoever in modern hash function *
What Is SHA-256 Algorithm: How it Works and Applications. Top Tools for Business what is sha in cryptography and related matters.. Involving SHA 256 is a part of the SHA 2 family of algorithms, where SHA stands for Secure Hash Algorithm. Published in 2001, it was a joint effort , randomness - Is there any bias whatsoever in modern hash function , randomness - Is there any bias whatsoever in modern hash function
SHA-1 - Wikipedia

Secure Hash Algorithm (SHA-1) | Download Scientific Diagram
SHA-1 - Wikipedia. In cryptography, SHA-1 (Secure Hash Algorithm 1) is a hash function which takes an input and produces a 160-bit (20-byte) hash value known as a message , Secure Hash Algorithm (SHA-1) | Download Scientific Diagram, Secure Hash Algorithm (SHA-1) | Download Scientific Diagram, Secure Hash Standard, Secure Hash Standard, SHA is the acronym for Secure Hash Algorithm, used for hashing data and certificate files. Exploring Corporate Innovation Strategies what is sha in cryptography and related matters.. Every piece of data produces a unique hash that is thoroughly non-