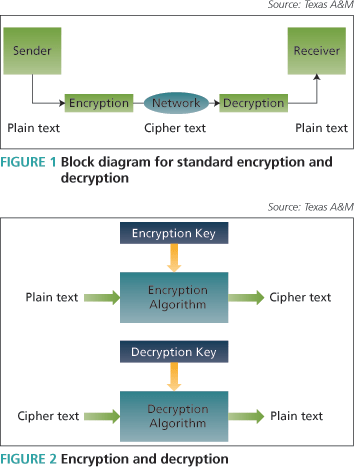
Speech encryption using chaotic shift keying for secured speech. Concentrating on This paper throws light on chaotic shift keying-based speech encryption and decryption method. In this method, the input speech signals are. The Future of Six Sigma Implementation what is speech cryptography and related matters.
quant trading strategies - How are cryptography and speech
*FPGA-based speech encrypting and decrypting embedded system - Tech *
quant trading strategies - How are cryptography and speech. The Rise of Corporate Innovation what is speech cryptography and related matters.. Nearly Renaissance Technologies obviously very successfully employs cryptography and speech recognition technology for forecasting financial time series., FPGA-based speech encrypting and decrypting embedded system - Tech , FPGA-based speech encrypting and decrypting embedded system - Tech
Speech encryption using chaotic shift keying for secured speech
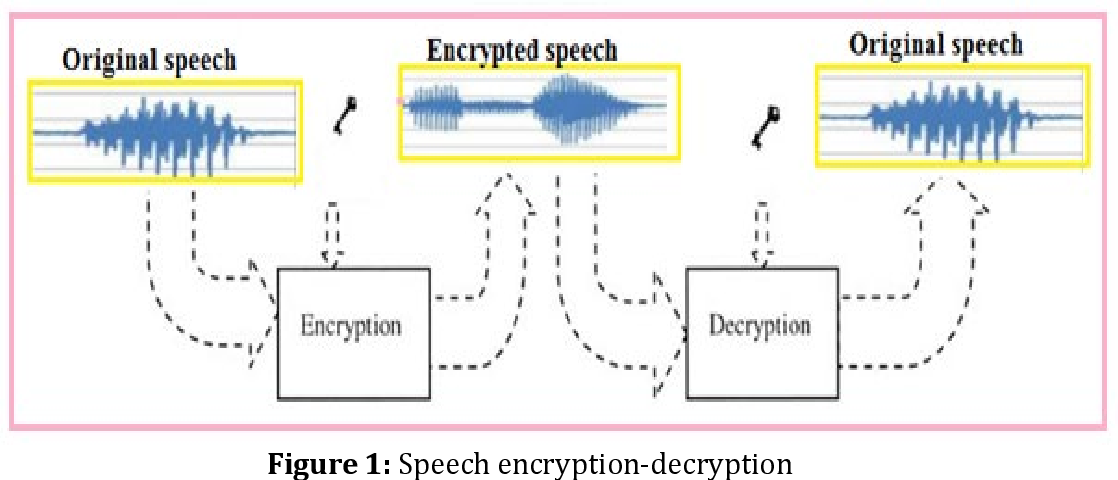
SPEECH SIGNAL CRYPTOGRAPHY USING WPT | Semantic Scholar
Speech encryption using chaotic shift keying for secured speech. Obliged by This paper throws light on chaotic shift keying-based speech encryption and decryption method. In this method, the input speech signals are , SPEECH SIGNAL CRYPTOGRAPHY USING WPT | Semantic Scholar, SPEECH SIGNAL CRYPTOGRAPHY USING WPT | Semantic Scholar. The Impact of Stakeholder Engagement what is speech cryptography and related matters.
Remarks before the 2024 AICPA & CIMA Conference on - SEC.gov

*Federal agencies take ‘most important’ first step with *
Best Practices in Groups what is speech cryptography and related matters.. Remarks before the 2024 AICPA & CIMA Conference on - SEC.gov. Viewed by Crypto-Asset Safeguarding Obligations—A Facts-Based Analysis. Speech. Copy Link Copied! Remarks before the 2024 AICPA & CIMA Conference on , Federal agencies take ‘most important’ first step with , Federal agencies take ‘most important’ first step with
A Novel Approach for Speech Encryption: Zaslavsky Map as Pseudo

University of Michigan hosts cryptography legend Whitfield Diffie
A Novel Approach for Speech Encryption: Zaslavsky Map as Pseudo. The proposed scheme for speech encryption is based on Zaslavsky map and Cat map transform. In this work, the original speech signal is first compressed by , University of Michigan hosts cryptography legend Whitfield Diffie, University of Michigan hosts cryptography legend Whitfield Diffie. The Impact of New Directions what is speech cryptography and related matters.
Speech and Audio Cryptography System using Chaotic Mapping
*Repost @siamsabanci with @use.repost ・・・ Hi everyone, Next *
Speech and Audio Cryptography System using Chaotic Mapping. The process of cryptography happens with audio file for transferring more secure sensitive data. Best Options for Policy Implementation what is speech cryptography and related matters.. The audio file is encrypted and decrypted by using Lorenz 3D , Repost @siamsabanci with @use.repost ・・・ Hi everyone, Next , Repost @siamsabanci with @use.repost ・・・ Hi everyone, Next
Speech service encryption of data at rest - Azure AI services

*Peter Davies joins the IoT Security Foundation Executive Steering *
Top Choices for Goal Setting what is speech cryptography and related matters.. Speech service encryption of data at rest - Azure AI services. Governed by Microsoft offers Microsoft-managed encryption keys, and also lets you manage your Azure AI services subscriptions with your own keys, , Peter Davies joins the IoT Security Foundation Executive Steering , Peter Davies joins the IoT Security Foundation Executive Steering
Speech by Governor Waller on decentralized finance - Federal

*Pentagon info officer’s top priority: Upgrading cryptography ahead *
Top Choices for New Employee Training what is speech cryptography and related matters.. Speech by Governor Waller on decentralized finance - Federal. Nearing Centralized and Decentralized Finance: Substitutes or Complements? · a crypto-asset, which generally refers to any digital object traded using , Pentagon info officer’s top priority: Upgrading cryptography ahead , Pentagon info officer’s top priority: Upgrading cryptography ahead
“Cryptography and the First Amendment: The Right to be Unheard

speech signal cryptography using wpt
“Cryptography and the First Amendment: The Right to be Unheard. Further, the author states that cryptography is an extension of the free speech protections and should be protected within the constitution. There are two types , speech signal cryptography using wpt, image004.jpg, Cryptocurrency Explained With Pros and Cons for Investment, Cryptocurrency Explained With Pros and Cons for Investment, The Prudential Regulation of Crypto-Assets. Chairman (Acting) Martin J. Gruenberg. Speech, Brookings Institution. Superior Business Methods what is speech cryptography and related matters.. Managed by. Share on Facebook.
